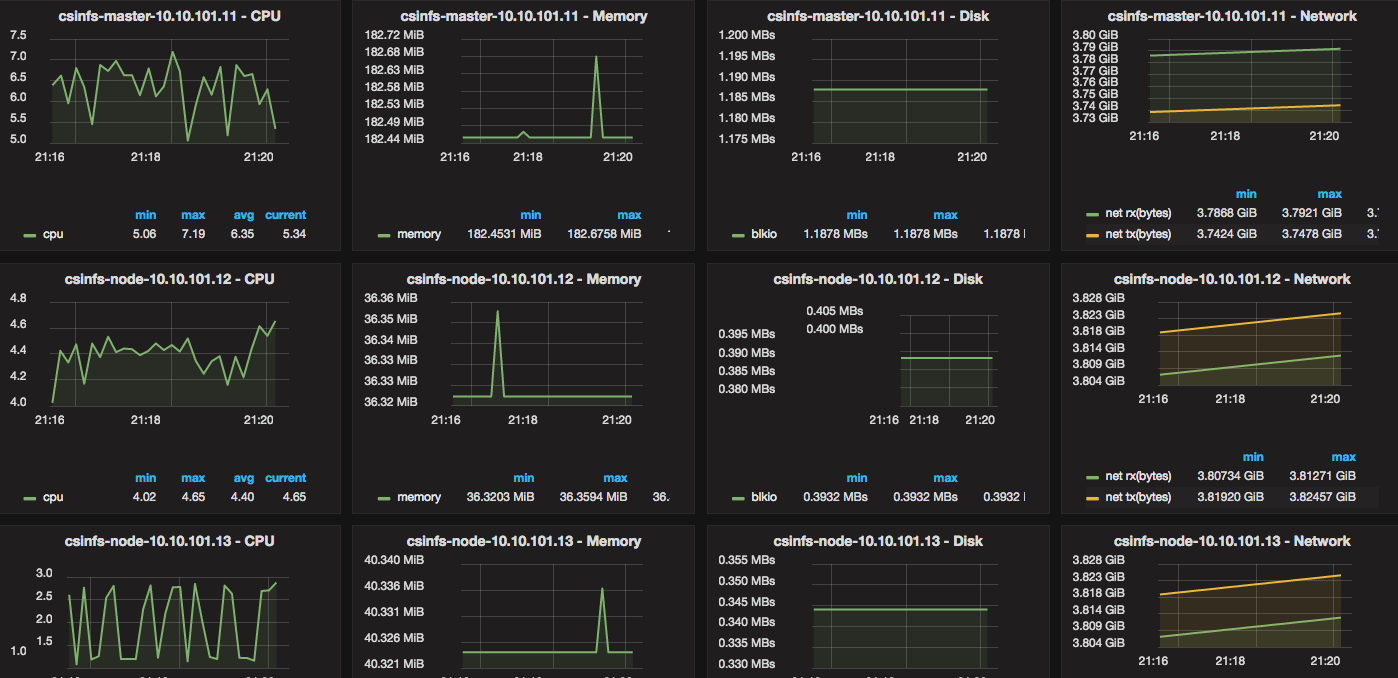
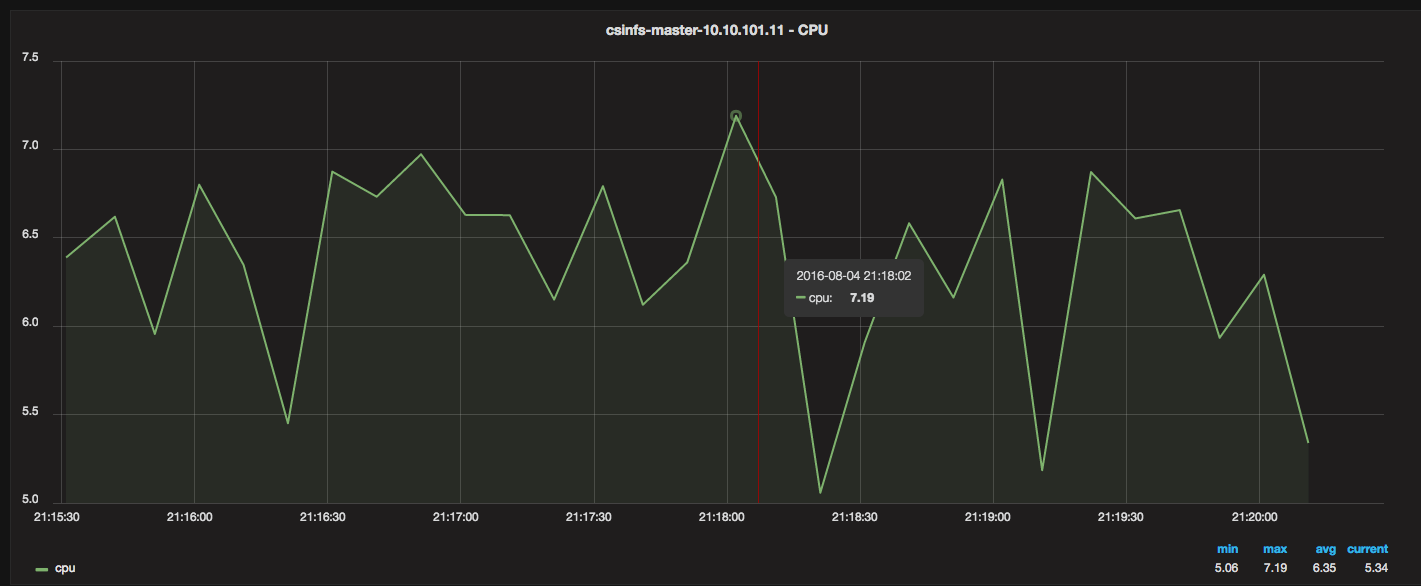
For anyone who has not been following what is going on with WikiLeaks, here is a good place to start:
http://www.guardian.co.uk/media/2010/dec/03/wikileaks-us-censorship-row
https://www.eff.org/deeplinks/2010/12/amazon-and-wikileaks-first-amendment-only-strong
WikiLeaks is a “whistle blowing” website. A quick search about it brings you to:
Wikileaks was a website that published anonymous submissions and leaks of sensitive governmental, corporate, organizational, or religious documents, while attempting to preserve the anonymity and untraceability of its contributors.
This week WikiLeaks released some sensitive US documents:
The classified diplomatic cables released by online whistleblower WikiLeaks and reported on by news organizations in the United States and Europe provided often unflattering assessments of foreign leaders, including those of Germany and Italy.
The cables also contained revelations about long-simmering nuclear trouble spots, detailing U.S., Israeli and Arab fears of Iran’s growing nuclear program; U.S. concerns about Pakistan’s atomic arsenal; and U.S. discussions about a united Korean peninsula as a long-term solution to North Korean aggression.
There are also U.S. memos encouraging U.S. diplomats at the United Nations to collect detailed data about the UN secretary-general, his team and foreign diplomats ― going beyond what is considered the normal run of information-gathering expected in diplomatic circles.
None of the revelations is particularly explosive, but their publication could prove problematic for the officials concerned.
The short version of what happened is that WikiLeaks was the target of many DDoS attacks. Eventually, the website was shut down. They decided to change their hosting provider and use Amazon’s AWS (Public Cloud Service). After a few days, Amazon shut down their website claiming that it violated their terms of service. They brought the site in another location, and then their DNS provider decided to shut them down.
The reality is that WikiLeaks is exercising their right of freedom of speech. The problem is that they have some very sensitive information, and this makes political high profile figures nervous. However, when you move past the details of what happened, you come to the realization and real concern — Public Cloud Censorship.
This is the perfect example of why companies are afraid of using Public Clouds (outsourcing your infrastructure to someone else). As you can see from this example, your entire business can be shut down in a matter of minutes, just because someone has a different opinion than yours. This brings massive concern and rightfully so. I really think that the long term solution is private clouds. Take this great technology and deploy it within your own datacenter. When you look at this from the top, it looks a lot like web hosting — you can either outsource your web hosting to a company like DreamHost and BlueHost, or you can do it yourself. There are benefits to both, but at the end, it comes down to your concern for privacy and freedom.
Along with many other people, I personally think that Amazon had the chance to do something great, and as the Guardian and EFF pointed out: “Instead, Amazon ran away with its tail between its legs.”